Download social engineering toolkit for windows.
Jika kamu mencari artikel download social engineering toolkit for windows terbaru, berarti kamu telah berada di website yang benar. Yuk langsung saja kita simak ulasan download social engineering toolkit for windows berikut ini.
 Using The Social Engineering Toolkit In Kali Linux Fixedbyvonnie From fixedbyvonnie.com
Using The Social Engineering Toolkit In Kali Linux Fixedbyvonnie From fixedbyvonnie.com
In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. Here in this tutorial Im only write how-to and step-by-step to perform the basic attack but for the rest you can modified it with your own imagination. It has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. The Social-Engineer Toolkit SET was created and written by Dave Kennedy the founder of TrustedSec.
It has been a standard in system performance monitoring for the Solaris platform over the last 10 years.
TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent. TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent. It has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. Install a Fake Virus.
 Source: youtube.com
Source: youtube.com
Install a Fake Virus. Because you know human stupidity can not be patched seriously. With over two million downloads it is the standard for social-engineering. The Social-Engineer Toolkit SET was created and written by Dave Kennedy the founder of TrustedSec. Use Set to Create a Malicious Web Link.
In this lab we will do the following.
TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent. SET has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. Use Set to Create a Malicious Web Link. Social Engineering Toolkit SET So based on the scenario above you can imagine that we dont even need the victims device i used my laptop and my phone.
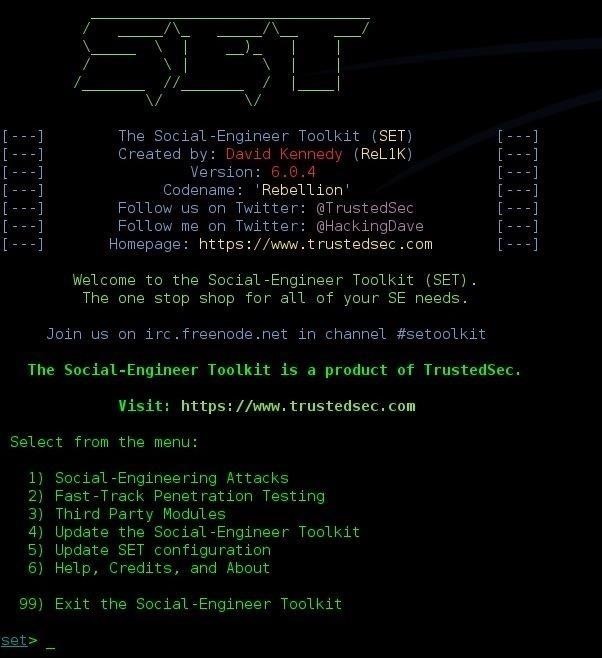 Source: null-byte.wonderhowto.com
Source: null-byte.wonderhowto.com
Because you know human stupidity can not be patched seriously. SET has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. With over two million downloads SET is the standard for social-engineering penetration tests and supported heavily within the security community. Download social-engineer-toolkit linux packages for Slackware.
 Source: securedyou.com
Source: securedyou.com
Social-Engineering toolkit available on backtrack like on backtrack 5 backbox blackbuntu Gnacktrack and other Linux distribution that are used for penetration testing. Here in this tutorial Im only write how-to and step-by-step to perform the basic attack but for the rest you can modified it with your own imagination. With over two million downloads it is the standard for social-engineering. 15 Steps to Hacking Windows Using Social Engineering Toolkit and Backtrack 5.
 Source: subscription.packtpub.com
Source: subscription.packtpub.com
Use Set to Create a Malicious Web Link. Comandos para ejecutar SET Social Engineering ToolkitEn el mundo de la seguridad informática no se puede de. The Social-Engineer Toolkit SET is specifically designed to perform advanced attacks against the human element. Install a Fake Virus.
As a condition. In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. It has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. Use Set to Create a Malicious Web Link.
Stack Exchange network consists of 176 QA communities including Stack Overflow the largest most trusted online community for developers to learn share their knowledge and build their careers.
Social Engineering Toolkit SET So based on the scenario above you can imagine that we dont even need the victims device i used my laptop and my phone. Install a Fake Virus. Here in this tutorial Im only write how-to and step-by-step to perform the basic attack but for the rest you can modified it with your own imagination. With over two million downloads SET is the standard for social-engineering penetration tests and supported heavily within the security community. The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment.

It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. Actually this hacking method will works perfectly with DNS spoofing or Man in the Middle Attack method. Download SE Toolkit for free. The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment.
The Social-Engineer Toolkit SET is an open-source penetration testing framework designed to perform advanced and quick attacks against targets. SET has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. The Social-Engineer Toolkit SET was created and written by Dave Kennedy the founder of TrustedSec. The Social-Engineer Toolkit v132 New version Download.
The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment.
Penetration testing framework. Create an addition VNC Session. Social Engineering Toolkit SET So based on the scenario above you can imagine that we dont even need the victims device i used my laptop and my phone. In this lab we will do the following.
 Source: sciencedirect.com
Source: sciencedirect.com
The SE Toolkit is a collection of scripts for performance analysis and gives advice on performance improvement. The Social-Engineer Toolkit is an open-source penetration testing framework designed for Social-Engineering. I only need his head and trust and stupidity too. The Social-Engineer Toolkit SET is specifically designed to perform advanced attacks against the human element.
 Source: youtube.com
Source: youtube.com
In this lab we will do the following. Because you know human stupidity can not be patched seriously. The Social Engineering Toolkit SET is a python-driven suite of custom tools which solely focuses on attacking the human element of penetration testing. Penetration testing framework.
 Source: hacking-tutorial.com
Source: hacking-tutorial.com
Stack Exchange network consists of 176 QA communities including Stack Overflow the largest most trusted online community for developers to learn share their knowledge and build their careers. Penetration testing framework. With over two million downloads SET is the standard for social-engineering penetration tests and supported heavily within the security community. The Social Engineering Toolkit SET is a python-driven suite of custom tools which solely focuses on attacking the human element of penetration testing.
Social-Engineering toolkit available on backtrack like on backtrack 5 backbox blackbuntu Gnacktrack and other Linux distribution that are used for penetration testing.
It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. The SE Toolkit is a collection of scripts for performance analysis and gives advice on performance improvement. The Social-Engineer Toolkit SET is specifically designed to perform advanced attacks against the human element. Microsoft Cognitive Toolkit CNTK CNTK describes neural networks as a series of computational steps via a digraph which are a set of n. As a condition.
 Source: securedyou.com
Source: securedyou.com
The Social-Engineer Toolkit SET was created and written by Dave Kennedy the founder of TrustedSec. SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time. Microsoft Cognitive Toolkit CNTK CNTK describes neural networks as a series of computational steps via a digraph which are a set of n. TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent. We will install Social Engineering Toolkit in windows subsystem Subscribe for moreI am following this guide.
Comandos para ejecutar SET Social Engineering ToolkitEn el mundo de la seguridad informática no se puede de.
I only need his head and trust and stupidity too. In this lab we will do the following. With over two million downloads SET is the standard for social-engineering penetration tests and supported heavily within the security community. It has been a standard in system performance monitoring for the Solaris platform over the last 10 years.
 Source: securedyou.com
Source: securedyou.com
The Social-Engineer Toolkit v132 New version Download. The Social-Engineer Toolkit v132 New version Download. Microsoft Cognitive Toolkit CNTK CNTK describes neural networks as a series of computational steps via a digraph which are a set of n. SET was written by David Kennedy ReL1K and with a lot of help from the community it has incorporated attacks never before seen.
 Source: securitytrails.com
Source: securitytrails.com
The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment. 15 Steps to Hacking Windows Using Social Engineering Toolkit and Backtrack 5. It has been a standard in system performance monitoring for the Solaris platform over the last 10 years. Capture a Forensics Memory and Hard Disk Image.
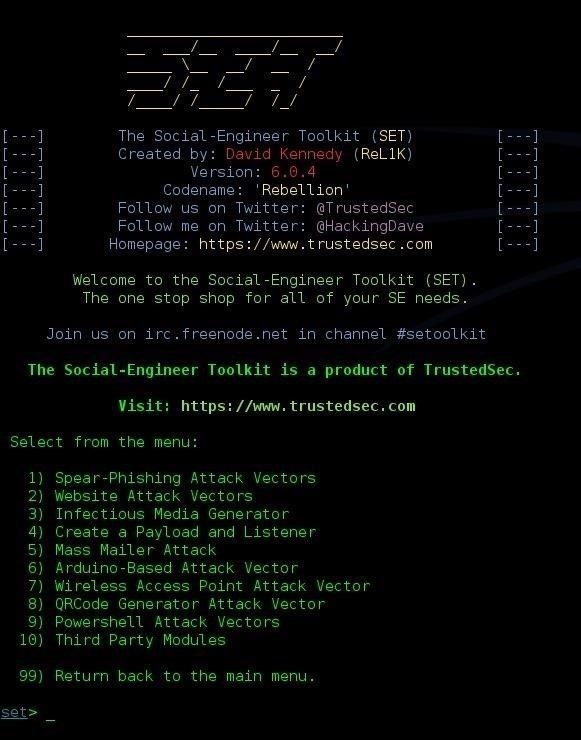 Source: null-byte.wonderhowto.com
Source: null-byte.wonderhowto.com
Download SE Toolkit for free. Microsoft Cognitive Toolkit CNTK CNTK describes neural networks as a series of computational steps via a digraph which are a set of n. SET was written by David Kennedy ReL1K and with a lot of help from the community it has incorporated attacks never before seen. The Social-Engineer Toolkit v132 New version Download.
It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering.
Use Set to Create a Malicious Web Link. It has been a standard in system performance monitoring for the Solaris platform over the last 10 years. In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. Install a Fake Virus. The SE Toolkit is a collection of scripts for performance analysis and gives advice on performance improvement.
 Source: securedyou.com
Source: securedyou.com
Actually this hacking method will works perfectly with DNS spoofing or Man in the Middle Attack method. Capture a Forensics Memory and Hard Disk Image. Penetration testing framework. With over two million downloads it is the standard for social-engineering. TrustedSec believes that social-engineering is one of the hardest attacks to protect against and now one of the most prevalent.
The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment.
Download social-engineer-toolkit linux packages for Slackware. SET has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. Penetration testing framework. Microsoft Cognitive Toolkit CNTK CNTK describes neural networks as a series of computational steps via a digraph which are a set of n.
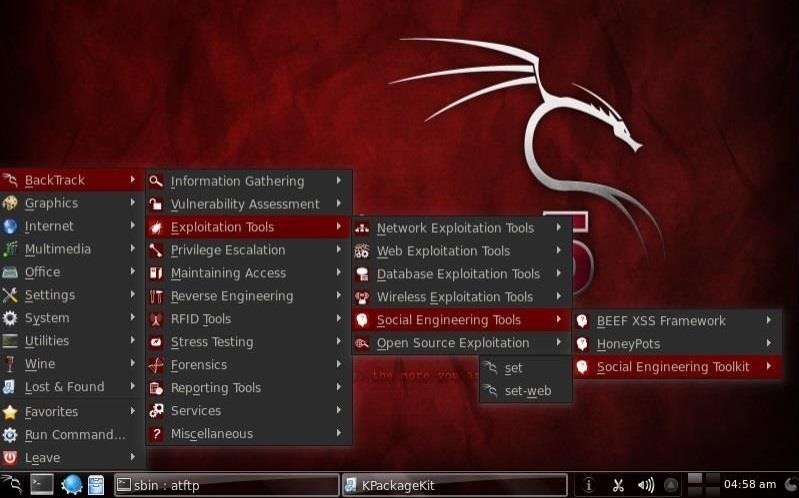 Source: null-byte.wonderhowto.com
Source: null-byte.wonderhowto.com
Capture a Forensics Memory and Hard Disk Image. The SE Toolkit is a collection of scripts for performance analysis and gives advice on performance improvement. SET has a number of custom attack vectors that allow you to make a believable attack in a fraction of the time. In this case we first are going to setup phishing Gmail Account login page in my Kali Linux and use my phone to. The Social-Engineer Toolkit has over 2 million downloads and is aimed at leveraging advanced technological attacks in a social-engineering type environment.

Stack Exchange network consists of 176 QA communities including Stack Overflow the largest most trusted online community for developers to learn share their knowledge and build their careers. SET was written by David Kennedy ReL1K and with a lot of help from the community it has incorporated attacks never before seen. SET has been presented at large-scale conferences including Blackhat DerbyCon Defcon and ShmooCon. It is an open-source Python-driven tool aimed at penetration testing around Social-Engineering. Install a Fake Virus.
 Source: goldenhacking.wordpress.com
Source: goldenhacking.wordpress.com
Social Engineering Toolkit SET So based on the scenario above you can imagine that we dont even need the victims device i used my laptop and my phone. The Social-Engineer Toolkit is an open-source penetration testing framework designed for Social-Engineering. Actually this hacking method will works perfectly with DNS spoofing or Man in the Middle Attack method. It has been a standard in system performance monitoring for the Solaris platform over the last 10 years. Comandos para ejecutar SET Social Engineering ToolkitEn el mundo de la seguridad informática no se puede de.
Situs ini adalah komunitas terbuka bagi pengguna untuk menuangkan apa yang mereka cari di internet, semua konten atau gambar di situs web ini hanya untuk penggunaan pribadi, sangat dilarang untuk menggunakan artikel ini untuk tujuan komersial, jika Anda adalah penulisnya dan menemukan gambar ini dibagikan tanpa izin Anda, silakan ajukan laporan DMCA kepada Kami.
Jika Anda menemukan situs ini bermanfaat, tolong dukung kami dengan membagikan postingan ini ke akun media sosial seperti Facebook, Instagram dan sebagainya atau bisa juga save halaman blog ini dengan judul download social engineering toolkit for windows dengan menggunakan Ctrl + D untuk perangkat laptop dengan sistem operasi Windows atau Command + D untuk laptop dengan sistem operasi Apple. Jika Anda menggunakan smartphone, Anda juga dapat menggunakan menu laci dari browser yang Anda gunakan. Baik itu sistem operasi Windows, Mac, iOS, atau Android, Anda tetap dapat menandai situs web ini.





